
Source: Linus Tech Tips YouTube Channel
Many of us know that the popular YouTube channel Linus Tech Tips got hacked a few days ago. Of course, none of us want to be in the same situation and get our session tokens stolen so the attacker (usually referred to as the “hacker”) can log in to our account without the password. Even if you have 2 Factor Authentication enabled, your account is still vulnerable to this attack. So, what’s the best way to avoid this?
Before we move on, we need to understand what a session token is and how it can be used to access an account without the need for a password.
Session Token
A session token is a random value generated by a server to identify a specific user for the duration of one interaction session.
Source: Metabase
Too complex? Let me simplify it for you.
When you log in to any website or web application using your browser, in common cases, the website or the web application creates a session token and uses that to keep you logged in. This is useful because nobody would like to enter the password every time they move to a new page of that website or application. It’s like a badge for a physical event. You need to give a lot of details to get the badge for the event, but once you get the badge, you can roam around freely inside the event venue (generally speaking). Session tokens are like those badges.
Now, once you get your badge (session token) by entering your details (password, even 2FA code), if someone steals the badge (session token), he/she can get access to the event (website or application) because *only* you are supposed to have that unique badge (session token).
No matter how hard the authentication method (login process, again generally speaking) is, once you are logged in, you have passed all your hurdles and until you log out, the token is gonna stay alive to keep you logged in. And if anyone else has access to your session token, they are gonna have access until you log out and the session tokens are invalidated.
What can you do? Throw your computer out of the window after you are done with the website or the application? Erm… not the best choice, really!
A realistic solution is clearing cookies and other site data once you are done with that website or application.
Doing this manually every time after visiting every website is not a very fancy task. We are human, and we can forget to clear the site data once we are done. The good news is, the Chrome browser has a native feature that can help you with this and you won’t need any additional software or plugin.
Steps:
Simply go to your Chrome Settings by clicking on the three dots in the top-right corner:
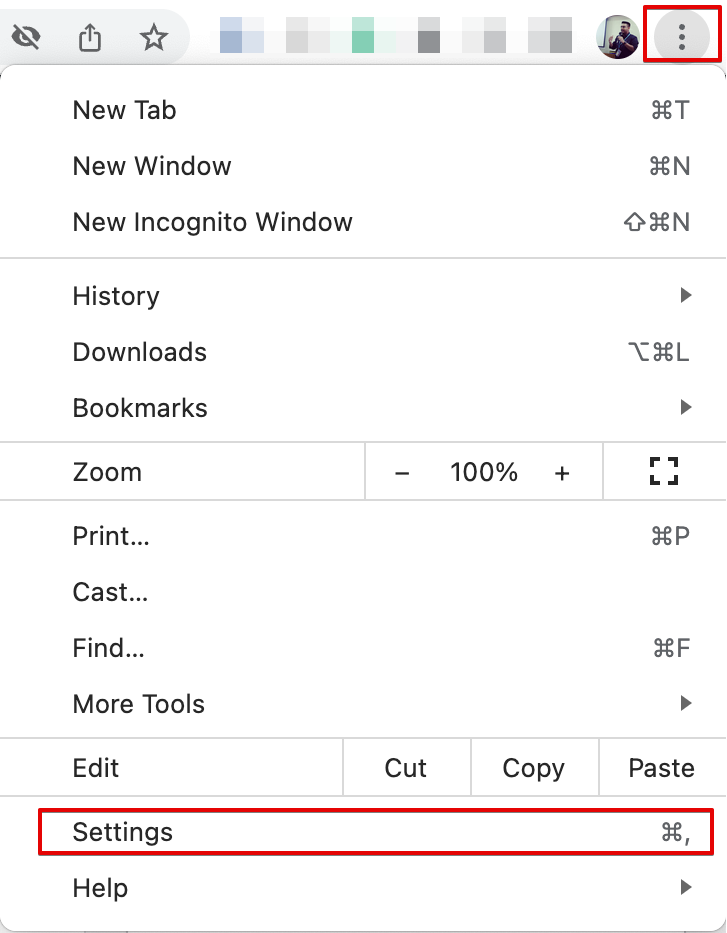
Then click on the “Privacy and Security” menu on the left sidebar. Then turn on the “Clear cookies and site data when you close all windows” option:
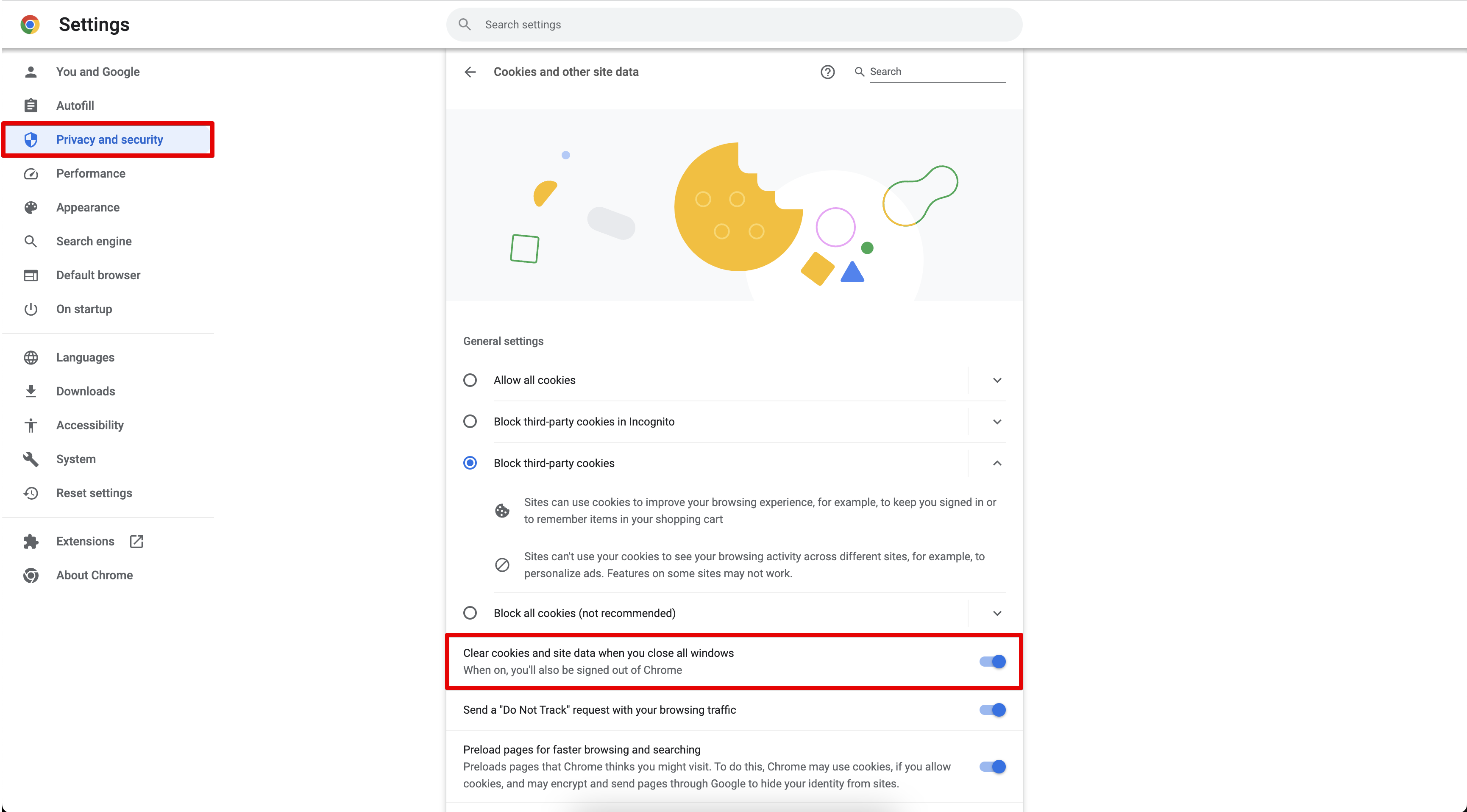
And that’s simply it! Chrome will clear all site data for you once you exit the browser.
The only caveat is – you will need to re-login to your accounts the next time you open the Chrome browser and visit that website or web application. But, it’s better to log in again (if you use a good password manager, this should be fairly easy) than losing access to your account or the attacker (again, usually referred to as the hacker) having access to your account.
Of course, only this won’t make your account fully safe from attacks, but this can help with other security practices like using a strong password, using 2 Factor Authentication, and/or using a hardware security token, etc.
Hope this will help. Feel free to leave a comment below with your opinion on this. Happy browsing! 🎉